Eacceptable Format to Upload Package to Lambda
* Latest update: June 21st, 2019.
AWS Lambda is the leading product when it comes to "serverless" computing, or Function as a Service (FaaS). With AWS Lambda, computing infrastructure is entirely managed past AWS, meaning developers can write lawmaking and immediately upload and run it in the cloud, without launching EC2 instances or whatever blazon of computing infrastructure.
This is a great thing, as it brings a lot of agility to product development. Nonetheless, running a reliable Lambda application in production requires you to yet follow operational best practices. In this article I am including some recommendations, based on my experience with operations in full general besides as working with AWS Lambda.
Permit'south start with what I see as rule #ane of AWS Lambda…
Just because AWS manages computing for you, doesn't mean Lambda is hands-off.
I've heard and read many comments that advise Lambda releases developers from the burden of doing operational work. Information technology doesn't. Using AWS Lambda only means you don't accept to launch, scale and maintain EC2 infrastructure to run your code in AWS (which is great). Just essentially everything else regarding operations remains the same, just packaged differently. Running an application on AWS Lambda that reliably generates revenue for your business requires the same amount of discipline equally any other software application.
… and here are some recommendations:
Monitor CloudWatch Lambda metrics
Every bit of today, there are 8 Lambda metrics bachelor in CloudWatch:
- Duration. This number is rounded upward to the nearest 100ms interval. The longer the execution, the more you lot will pay. You too take to make certain this metric is not running dangerously close to the function timeout. If this is the case, either notice ways for the function to run faster, or increase the office timeout.
- Errors. This metric should be analyzed relative to the
Invocationsmetric. For example, information technology's non the same to come across 1,000 errors in a function that executes 1 million times a twenty-four hour period compared to a office that executes 10,000 times a 24-hour interval. Is your application's acceptable mistake charge per unit 1%, 5%, ten% inside a period of time? The good news is that CloudWatch now supports metric math (i.eastward. Errors/Invocations), therefore y'all tin now monitor your functions and configure alarms based on error rates. Later in this commodity, I will cover Lambda'south retry behavior in instance of errors. - Invocations. Apply this metric to decide your fault tolerance, as mentioned to a higher place. If your Invocations modify, your alarming on Errors should change every bit well, in order to proceed your error tolerance % constant. This metric is also good to keep an centre on toll: the more invocations, the more you will pay. To forecast pricing, consider not but invocations just too the retentiveness you have allocated to your function, since this impacts the GB-second you will pay for your functions. Also, when practice zero invocations first to tell y'all in that location'southward something incorrect? 5 minutes, 1 hour, 12 hours? I recommend setting up alarms when this number is zero for a period of time. Zip invocations likely means there is a problem with your function trigger.
- Throttles. So y'all have a pop function, correct? If you wait your function executions to exist above 1000 concurrent executions, then submit a limit increase in AWS - or you'll risk experiencing throttled executions. This should be part of your regular chapters planning. I recommend to set up alarms when the Invocations metric for each function is close to the number you have assigned in your capacity planning exercise. If your office is beingness throttled, that'due south obviously bad news, so you should alarm on this metric. Something useful to consider is that you can assign reserved concurrency to a particular office. If you accept a disquisitional function, you can increase its availability by assigning a reserved concurrency value. This way disquisitional functions will not be affected by high concurrency triggered by other less critical functions.
- DeadLetterErrors. Lambda gives you lot a dandy characteristic called Expressionless Letter Queue. Basically it allows you to write the payload from failed asynchronous executions to an SQS queue or SNS topic of your choice, then it tin be processed or analyzed later. If for some reason you can't write to the DLQ, you should know about it. That's what the DLQ Errors metric tells you. Lambda increments this metric each time a payload can't exist written to the DLQ destination.
- IteratorAge. You take Lambda functions that procedure incoming records from either Kinesis or Dynamo DB streams. Y'all want to know as soon as possible when records are not processed as rapidly as they need to. This metric will help yous monitor this and foreclose your applications from building a dangerous backlog of unprocessed records.
- ConcurrentExecutions. Measures the number of concurrent executions for a detail function. Information technology's of import to monitor this metric and brand certain that you're not running close to the Concurrent Executions limit for your AWS account or for a particular office - and avoid throttled Lambda executions.
- UnreservedConcurrentExecutions. Similarly to the previous metric, only this one allows you to know how close you're getting to your Lambda concurrency limit.
Allocate the correct memory for your part
Do you come across anything incorrect with this message?
Duration: 702.16 ms Billed Duration: 800 ms Retentiveness Size: 512 MB Max Memory Used: 15 MB
This log entry is proverb that you might be paying for over-provisioned capacity. If your part consistently requires 15MB of retentiveness, you should consider allocating less retention, non 512MB. Here is a price comparing betwixt two configurations, assuming 100 million monthly executions:
| Memory (MB) | 100 million x 800ms |
|---|---|
| 128 | $186.67 |
| 512 | $686.67 |
If you think 100 million executions is a big number, you're right. Only in one case you starting time using Lambda seriously, for processing CloudTrail records, Billing, Kinesis, S3 events, API Gateway and other sources, you lot will see that executions add upwardly really fast and y'all'll easily attain 100 million monthly executions.
If you were using this office at a rate of 100 meg executions per calendar month, you would pay approximately $viii,240 per year instead of $2,240. That's coin you lot could utilize on more valuable things than an over-provisioned Lambda function.
That being said, allocating more retentiveness oft means your function will execute faster. This is because AWS allocates more CPU ability proportionally to memory size. You lot can read more details here. If almost of your function's execution time is spent doing local processing (instead of waiting for external components to consummate), having more memory will likely upshot in faster executions - and potentially lower price.
Therefore, my recommendation is to examination your function with different memory allocations, so measure execution time and calculate cost at scale. Just brand sure the part is already warmed up, so y'all tin can measure the right execution time. Y'all can find more details about Lambda function initialization here.
Useful CloudWatch Logs Features
Metric Filters
The AWS Lambda service automatically writes execution logs to CloudWatch Logs. CloudWatch Logs has a very cool feature called Metric Filters, which allow you to place text patterns in your logs and automatically convert them to CloudWatch Metrics. This is extremely handy, so you can easily publish awarding metrics to CloudWatch. For example, every fourth dimension the text "submit_order" is found in CloudWatch Logs, you lot could publish a metric called "SubmittedOrders". You can and so create an warning if this metric drops to zero inside a period of time.
Something very important about using Metric Filters is that equally long equally there is a consistent, identifiable blueprint in your Lambda function output, you don't need to update your part code if y'all want to publish more custom CloudWatch metrics. All you lot have to practice is configure a new Metric Filter. Even better, Metric Filters are supported in CloudFormation templates, so you lot tin can automate their creation and keep track of their history.
CloudWatch Logs Insights
CloudWatch Logs Insights is a neat tool you can use to operate your Lambda functions. It offers a powerful query syntax and platform that you lot can use to filter Lambda logs by timestamp and by text patterns. You can besides export your findings to CloudWatch Dashboards or text files for farther analysis.
When something fails, make sure there is a metric that tells you most it
When it comes to operations, nothing is more dangerous than existence blind to errors in your system. Therefore, you should know in that location are fault scenarios in Lambda that don't upshot automatically in an Error metric in CloudWatch.
Here are some examples:
- Python. Unhandled Exceptions outcome automatically in a CloudWatch Fault metric. If your code swallows exceptions, in that location volition exist no record of it and your function execution will succeed, even if something went wrong. Logging errors using
logger.errorwill simply outcome in an [ERROR] line in CloudWatch Logs and not automatically in a CloudWatch metric, unless you create a Metric Filter in CloudWatch Logs that searches for the text pattern "[ERROR]". - NodeJS v4.3. If the function ends with a
callback(mistake)line, Lambda will automatically study an Mistake metric to CloudWatch. If you stop withpanel.error(), Lambda volition only write an mistake bulletin in CloudWatch Logs and no metric, unless you configure a Metric Filter in CloudWatch Logs. - NodeJS v0.10.42 If yous don't call
context.succeed(Object consequence)orcontext.done(Error mistake, Object result)to indicate function completion, you will get the infamous "Process exited before completing asking" error. At least this error results automatically in a CloudWatch Error metric, simply often lacks context for constructive troubleshooting. If you end the execution withcontext.fail(Fault mistake)you lot will likewise go an automatic CloudWatch Mistake metric.
You lot can also use Metric Filters to identify application errors.
Know what happens "under the hood" when a Lambda function is executed
AWS uses container technology that assigns resource to each Lambda part. Therefore, each function has its own surround and resources, such equally memory and file system. When you execute a Lambda function, two things tin happen: 1)a new container is instantiated, 2)an existing container is used for this execution.
You lot have no control on whether your execution will run on a new container or an existing container. Typically, functions that run in quick succession are executed on an existing container, while sporadic functions need to wait for a new container to be instantiated. Therefore, there is a difference in operation in each scenario. The difference is typically in the millisecond range merely it will vary by function.
Likewise, it'south important to differentiate betwixt 1)part and two)function execution. While a office has its own isolated environment (container), multiple function executions can share resources allocated to their respective office. Therefore, it is possible that function executions <ahref="http://weblog.matthewdfuller.com/2015/12/aws-lambda-occasionally-reliable-caching.html" target="new">admission each other'south data.
I recommend the following:
- Run a load examination for your detail function and measure out how long information technology takes to execute during the first few minutes, compared to successive executions. If your apply case is very fourth dimension sensitive, container initialization time might get an operational issue.
- Never use global variables (those outside your function handler) to shop any type of sensitive data, or information that is specific to each function execution.
- Enable AWS X-Ray in guild to identify potential bottlenecks in your Lambda execution. 10-Ray can be useful when trying to visualize where you're spending your function's execution time.
Treat outcome triggers, functions and final targets as a single environment (dev, test, prod, etc.)
In an issue-driven architecture, Lambda functions are not isolated components. Typically Lambda functions are an intermediate step between an consequence and a final destination. Lambda functions tin can be automatically triggered by a number of AWS services (i.e. API Gateway, S3 events, CloudWatch Events, etc.) The Lambda function either transforms or forrard asking data to a final target (i.due east. S3, Dynamo, Elasticsearch, etc.) Some events incorporate simply a reference to the data, while other events contain the data itself.
Something similar this:
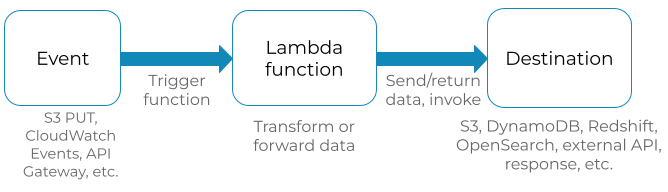
Ideally, in that location should be independent stages that contain their ain set of AWS components for events, functions and data stores. For most system owners this is an obvious point. However, I've seen operational issues that stemmed from not following this basic principle.
This is probably due to how quick it is to build a service from the ground upwardly using Lambda, that information technology's also like shooting fish in a barrel to forget most operational best practices.
There are frameworks y'all can use to alleviate this problem, such as Serverless, Beaker or ClaudiaJS. You need to keep rails of each component's version and grouping them into a unmarried environment version. This practice is really not too dissimilar from what you would need to do in any service oriented compages earlier Lambda.
There is also the AWS Serverless Application Model, which allows you to ascertain multiple components of your serverless application (API Gateway, S3 events, CloudWatch Events, Lambda functions, Dynamo DB tables, etc.) as a CloudFormation stack, using a CloudFormation template. SAM has saved me a LOT of fourth dimension when defining the AWS components in my serverless applications. I actually recommend giving information technology a attempt.
The AWS Lambda panel offers a very helpful consolidated view of your Lambda functions, where yous can see all components related to your Lambda functions, grouped as Applications. Information technology's definitely worth becoming familiar with it.
Don't utilise the AWS Lambda panel to develop Production lawmaking
The AWS Lambda console offers a spider web-based code editor that you tin use to become your role upwardly and running. This is great to go a feel of how Lambda works, but it's neither scalable nor recommended.
Here are some disadvantages of using the Lambda panel code editor:
- You don't get lawmaking versioning automatically. If you brand a bad mistake and striking the Save push, that's information technology, your working code is gone forever.
- You don't get integration with GitHub or whatever other code repository.
- You can't import modules beyond the AWS SDK. If y'all need a specific library, you volition take to develop your function locally, create a .nix file and upload it to AWS Lambda - which is what y'all should exist doing from the beginning anyways.
- If you're not using versions and aliases, you're basically tinkering with your Alive production code with no safeguard whatsoever! Did I mention at that place is no version control?
Actually, if yous're using the AWS panel to set upward your serverless components, you're doing it wrong.
I affair about serverless applications is that the number of components can explode very quickly. For example, the number of functions and their corresponding triggers and data sources can apace turn into an unmanageable mess. That'south why it's very important to utilise tools such as the Serverless Application Model, where y'all ascertain everything every bit code.
I only use the AWS Lambda console to listing my Lambda functions and look at some metrics, and pretty much naught else.
Examination your function locally
Since you lot shouldn't employ the Lambda console lawmaking editor, you'll take to write your code locally, parcel it into a .cipher file and deploy information technology to Lambda. Even though you can hands automate these steps, it'due south notwithstanding a tedious procedure that you'll want to minimize.
That's why y'all'll want to exam your part before you lot upload information technology to AWS Lambda. Thankfully, in that location are tools that let you test your function locally, such equally Python Lambda Local, or Lambda Local (for NodeJS). These tools let you create event and context objects locally, which y'all can employ to create examination automation scripts that volition requite you a adept level of conviction before you upload your function code to the cloud.
And at that place'due south also SAM Local, the official AWS CLI-based tool to test your functions locally, using Docker.
You should consider these local tests equally your first gate, but not your only one. And this takes us to the next betoken…
Automate integration tests and deployments, but similar whatever other piece of software
With AWS Lambda, you can implement a typical Continuous Integration flow and automate information technology using a service such every bit AWS Code Pipeline or whatsoever CI tool of your option. A mutual flow would await like this:
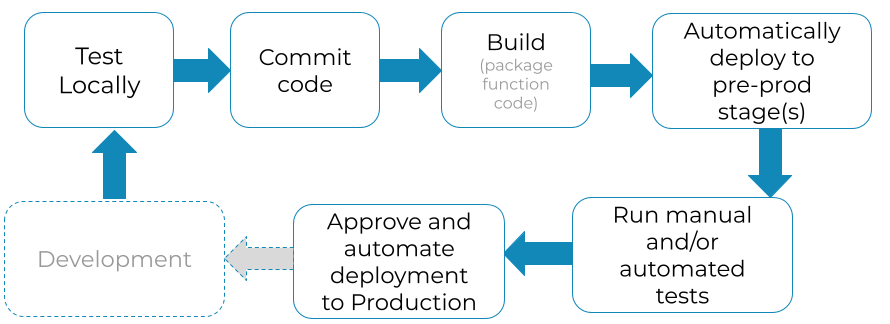
I really recommend using Serverless Application Model (SAM) + CodeBuild + Code Pipeline, together. SAM makes the definition and creation of serverless resource easy, using CloudFormation syntax. CodeBuild simplifies the creation of deployment packages. Using CodeBuild you'll avert some annoying errors that can pop up when yous build your code in a local surroundings that is not running on EC2 and Amazon Linux. And finally, Code Pipeline orchestrates the different steps required in your awarding deployment.
Using these 3 components together, I tin can literally go from local code to a full Lambda deployment, with a single CLI control. No demand to configure serverless components in the AWS console, create a .cipher file, upload it and then run deployment commands and other things. I tin can simply sit, relax and let Code Pipeline do the work for me. Code Pipeline has saved me countless hours of tedious, manual piece of work.
One important consideration for critical environments (such every bit Production) is to use the AWS CodePipeline Manual Approval characteristic before deploying to Production. Ideally, your pipeline should create a CloudFormation Change Set that tin can be reviewed and approved manually earlier the final deployment to Production. I can say that reviewing Modify Sets has helped me prevent bad deployments in the past.
Make sure your local development environment has exactly the same permissions that yous have assigned to your Lambda function
One of the almost disquisitional configurations for your Lambda function are the IAM permissions that yous assign to information technology. For example, if your function writes objects to S3, information technology must have an IAM Role assigned to it that grants Lambda permissions to telephone call the PutObject S3 API. The aforementioned is true for whatever other AWS APIs that are invoked from your Lambda function. If the function tries to call an AWS API it doesn't have permissions for, it volition become an Access Denied exception. The all-time practice is to assign only the necessary IAM permissions to your functions and aught else.
The problem is, many developers configure local environments using IAM credentials that have full access to AWS APIs. This might be OK in your dev environment using a dev AWS account, but it's definitely non good for a Production environment. It's common that a programmer tests a office locally, in a dev environment with full privileges. So uploads the function to Production, where the part has a limited permissions scope (every bit it should) and then run into Access Denied exceptions.
I've seen this issue happen enough times, therefore I'one thousand including it in this article. To avoid this situation, make sure your local dev environs has exactly the same IAM permissions that you take granted your Lambda office in Production.
Understand the retry beliefs of your architecture in instance of function failure
Yous tin can configure a number of AWS triggers to invoke your Lambda function. Just what happens when your Lambda execution fails? (note I use the discussion "when" and non "if"). Before yous decide if a particular role trigger is a skillful fit for your application, you lot must know how they handle Lambda function failures.
A Lambda role can exist invoked in 2 ways, which issue in a different error retry behavior:
- Synchronously. Retries are responsibility of the trigger.
- Asynchronously. Retries are handled by the AWS Lambda service.
Hither are some examples of AWS triggers and what they do if their corresponding Lambda part fails:
| AWS Trigger | Invocation | Failure Behavior |
|---|---|---|
| S3 Events | Asynchronous | (N/A in AWS documentation) |
| Kinesis Streams | Synchronous | Retry until success. Blocks stream until success or data expiration (24 hours to 7 days) |
| SNS | Asynchronous | Up to 3 retries |
| SES | Asynchronous | (Due north/A in AWS documentation) |
| AWS Config | Asynchronous | (Northward/A in AWS documentation) |
| Cognito | Synchronous | (North/A in AWS documentation) |
| Alexa | Synchronous | (N/A in AWS documentation) |
| Lex | Synchronous | (N/A in AWS documentation) |
| CloudFront (Lambda @ Edge) | Synchronous | (N/A in AWS documentation) |
| Dynamo DB Streams | Synchronous | Retry until success. Blocks stream until success or information expiration (24 hours). |
| API Gateway | Synchronous | API Gateway returns error to client. |
| CloudWatch Logs Subscriptions | Asynchronous | (N/A in AWS documentation) |
| CloudFormation | Asynchronous | (Northward/A in AWS documentation) |
| CodeCommit | Asynchronous | (N/A in AWS documentation) |
| CloudWatch Events | Asynchronous | (N/A in AWS documentation) |
| AWS SDK | Both synchronous and asynchronous | Your application specifies retry behavior |
You can also use this information to cull the right criteria for CloudWatch Alarms. For example, a single failure that blocks a whole Kinesis stream is likely a serious outcome and you might desire to lower your alarm threshold. Merely you might desire to have a different alarming criteria for a single failure in a function triggered by SNS, when you know it volition be retried up to 3 times.
You tin read more than about Lambda event sources hither and about retry behaviour here.
In case of failure, don't forget to use Dead Letter Queues
If your Lambda functions are invoked asynchronously, Dead Letter Queues are a great way to increment availability. DLQs let you to send the payload of failed Lambda executions to a destination of your choice, which tin be an SQS queue or an SNS topic. AWS Lambda retries asynchronous executions up to 2 times, after that it sends the payload to a DLQ. This is corking for failure recovery, since yous can reprocess failed events, analyze them and set up them. Here are some examples where DLQs could exist very useful:
- Your downstream systems fail, which makes your Lambda execution to fail. In this instance, you tin can ever recover the payload from failed executions and re-execute them once your downstream systems recover.
- You run across an application error, or edge case. Y'all can always analyze the records in your DLQ, correct the trouble and re-execute as needed.
And in that location's also the DLQ Errors CloudWatch metric, in instance you can't write payloads to the DLQ. This gives yous even more protection and visibility to chop-chop recover from failure scenarios.
Don't be too permissive with IAM Roles
As you might know, when you lot create a Lambda role y'all have to link an IAM Role to information technology. This IAM role gives the function permissions to execute AWS APIs on your behalf. In social club to specify which permissions, you attach a policy to each role. Each policy includes which APIs tin can be executed and which AWS resource can be accessed by these APIs.
My primary bespeak is, avoid an IAM access policy that looks like this:
{ "Version": "2012-ten-17", "Statement": [ { "Effect": "Allow", "Activeness": "*", "Resource": "*" } ] } A Lambda function with this policy can execute whatsoever type of operation on any type of AWS resource, including accessing keys in KMS, creating more admin IAM roles or IAM users, terminating all your EC2 instances, accessing customer data stored in Dynamo DB or S3, etc. Let's say you have a Lambda role under evolution with this access policy. If that's the case, yous're basically opening a door to all your AWS resource in that account, to any developer or contractor in your organization.
Even if y'all trust 100% the members of your squad (which is OK) or you are the only developer in your AWS account, an over-permissive IAM Role opens the door to potentially devastating, honest mistakes such as deleting or updating certain resources.
Here are some ways to minimize risks associated with granting IAM permissions to your Lambda functions:
- Not everyone in your company should take permissions for creating and assigning IAM Roles. You only take to be careful and avert creating too much bureaucracy or slowing down your developers.
- Outset with the minimum set of IAM permissions and add together more every bit your function needs them.
- Audit IAM Roles regularly and make sure they don't give more than permissions than the Lambda function needs.
- Use CloudTrail to audit your Lambda functions and wait for unauthorized calls to sensitive AWS resource. I created a CloudFormation template for this - you can read more virtually information technology in this article.
- Use different accounts for development, test and production. There is some overhead that comes with this approach, simply in general information technology is the best fashion to protect your production environments from unintended access or privilege escalation.
Restrict who tin can call your Lambda functions
Depending on how IAM Roles and IAM Users are created in your AWS account, it'south possible that a number of entities have elevated permissions - including the rights to invoke any Lambda office in your account. To farther restrict who can invoke a particular office, yous accept the option to configure Lambda Resources Policies.
In addition to Resource Policies, you can configure CloudTrail to track non only the APIs called by your functions, but also which entities have invoked your Lambda functions.
Have a clean separation betwixt dissimilar versions and environments
Versions and aliases
As your office evolves, AWS Lambda gives you the option to assign a version number to your function at that particular point in time. Yous can remember of a version every bit a snapshot of your Lambda function. Versions are used together with aliases, which are a proper noun you can use to point to a particular version number. Versions and aliases are very useful as ways to define the stage your function lawmaking belongs to (i.east. DEV, Test, PROD)
Something like this:

By using versions and aliases, y'all tin can promote your lawmaking between test stages, exam it and promote it to PROD when you're set. This process can be automatic, using the AWS API and using Continuous Integration tools. All of this can make your deployment procedure less painful too equally reduce human error in your operations.
Also, if y'all're using CodeDeploy (which I really recommend), you can fix up a deployment pipeline that gradually shifts traffic to a new version of your Lambda function. This fashion y'all tin can minimize customer impact in case there are problems with your latest deployment. Y'all tin also automate rollback to the previous working version based on CloudWatch alarms. More information on this feature tin exist found hither.
Employ dissever AWS accounts
Another pick is to employ carve up AWS accounts for development/test and product environments. Having dissimilar AWS accounts too reduces the possibility of homo error on production environments and it helps with providing product access to the right IAM entities. You tin too utilise automated CI/CD tools to deploy your code to different AWS accounts. For critical systems, this is my preferred option.
Use Environment Variables (and Parameter Store) to separate code from configuration
If you lot're building a serious software component, most likely yous already avert whatsoever type of hard-coded configuration in your code. In the "server" world, an like shooting fish in a barrel solution is to proceed configurations somewhere in your file system or environment variables and access those values from your lawmaking. This gives a nice separation betwixt application code and configuration and information technology allows you to deploy code packages across different stages (i.eastward. DEV, Exam, PROD) without irresolute application lawmaking - but configurations.
Only how do you practice this in the "serverless" world, where each function is stateless? Thankfully, AWS Lambda offers the Environment Variables feature for this purpose.
You can utilise EC2 Parameter Shop to store the bodily values and use Environment Variables to store a reference to the object stored in Parameter Store. Even better, if you're handling secrets you can use AWS Secrets Manager together with Parameter Store.
Brand sure you can quickly roll back any lawmaking changes
Deploying lawmaking to production is NEVER hazard free. There's e'er the possibility of something going wrong and your customers suffering every bit a consequence. While you can't eliminate the possibility of something bad happening, you can always make it easier to roll back any broken code.
Versions and aliases are extremely handy in example of an emergency rollback. All you lot accept to practice is signal your PROD allonym to the previous working version and that's it. No need to checkout your previous working code, goose egg it and re-deploy it to AWS Lambda.
Consider using AWS Lambda Layers
Lambda Layers is a feature that can simplify the management of code packages that go into a Lambda function. Like any other dependencies, it has to be treated with caution, since updates to Layers can potentially affect multiple applications. That being said, Layers can simplify the rollout and operations of Lambda functions.
Examination for performance
AWS promises high scalability for your Lambda functions, just there are still resource limits yous should exist aware of. One of them is that past default y'all can't have more 1000 concurrent function executions - if you need a higher value you can submit a Service Limit Increment to AWS Back up, though. Each execution has limits as well. In that location is a limit to how much data you can store in the temporary file system (512MB), the number of threads or open up files (ane,024). The maximum immune execution time is 900 seconds (fifteen minutes) and there are limits to the request and response payload size (6MB for synchronous invocations, 256KB for asynchronous).
Therefore, I strongly recommend yous identify both steady and peak load scenarios and execute performance tests on your functions. This will give you confidence that your expected usage in Production doesn't exceed any of the Lambda resource limits.
When executing performance tests, you should quantify the execution time and frequency, so you can estimate the monthly cost of your office, given your expected usage in Production. Also, this is a adept fourth dimension to apply tools like AWS X-Ray in club to identify performance bottlenecks and fine-melody your application.
Estimate Toll at Calibration
AWS Lambda offers ane million costless executions, and each boosted million costs only $0.xx. When it comes to price, Lambda is a no-brainer, right? Well, non really. There are situations where Lambda pricing can be substantially higher compared to running your workload using EC2. If you lot have a process that runs infrequently, then Lambda will ever be cheaper compared to EC2. But if you accept a resource-intensive procedure that runs all the time, at high volume, that's when going serverless might cost you more than compared to EC2.
Permit'south say you have a function that runs at a book of 100 transactions per 2d (approximately 259 meg executions per month). Each execution consumes 1000ms and requires 512MB of retention. Y'all would pay approximately $2,210/month for this role. Let's say that yous can handle the same workload with a cluster of 10 m5d.large instances (SSD local storage), in which case you would pay $815/month.
The difference? This Lambda function would cost you $xvi,740 more per year compared to EC2.
The following table shows the monthly toll of a function that executes at 100 TPS, based on different combinations of execution fourth dimension and assigned memory (not counting the free tier).
| ms | 128MB | 512MB | 1024MB |
|---|---|---|---|
| 100 | $105.76 | $267.63 | $483.47 |
| 500 | $321.59 | $one,130.97 | $2,210.14 |
| chiliad | $591.38 | $2,210.fourteen | $4,368.48 |
Don't forget near CloudWatch Logs Price
Lambda functions write their output to CloudWatch Logs, which has a cost of $0.l/GB for ingested data and $0.03/GB for data storage. Let's take a look at the post-obit table, which shows different monthly cost for CloudWatch Logs ingestion based on Lambda Transactions Per Second and log message payload (KB) sent to CloudWatch Logs per Lambda execution:
| TPS | 1KB | 128KB | 256KB |
|---|---|---|---|
| 1 | $13 | $166 | $332 |
| x | $130 | $1,659 | $3,318 |
| 100 | $i,296 | $xvi,589 | $33,178 |
Equally you tin can see, CloudWatch Logs ingestion can actually cost more than than Lambda executions. I've seen many cases in Product where this is the case, so it'southward definitely something to be aware of before typing that console.log(...) statement.
Conclusions
- Lambda is a slap-up AWS product. Removing the need to manage servers is a great thing, but running a reliable Lambda-based application in Production requires operational discipline - just similar whatever other piece of software your business concern depends on.
- Lambda (aka FaaS or serverless) is a new prototype and information technology comes with its ain set up of challenges, such equally configurations, understanding pricing, treatment failure, assigning permissions, configuring metrics, monitoring and deployment automation.
- It is important to perform load tests, understand Lambda pricing at scale and brand an informed decision on whether a FaaS architecture brings the correct residuum of operation, price and availability to your awarding.
Are you because using a serverless compages, or already have 1 running?
I can certainly aid y'all with designing, implementing and optimizing your serverless components. But click on the Schedule Consultation button beneath and I'll exist happy to accept a chat.
Source: https://www.concurrencylabs.com/blog/how-to-operate-aws-lambda/
0 Response to "Eacceptable Format to Upload Package to Lambda"
Post a Comment